Apple Quietly Releases Safari 6.1.3 and Safari 7.0.3
Posted on
by
Derek Erwin
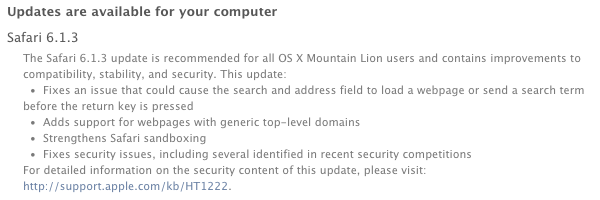
Yesterday, Apple quietly released Safari 6.1.3 and Safari 7.0.3 with security updates that address multiple vulnerabilities. These updates patch 27 security bugs altogether, all of which are related to arbitrary code execution.
Safari 6.1.3 and Safari 7.0.3 updates are available for: OS X Lion 10.7.5, OS X Lion Server 10.7.5, OS X Mountain Lion 10.8.5, and OS X Mavericks 10.9.2.
The Safari updates address arbitrary code execution issues mostly caused by “multiple memory corruption issues that existed in WebKit,” and another was due to “a logic issue that existed in the handling of IPC messages from the WebProcess,” according to Apple’s security bulletin.
Apple further described the vulnerabilities patched in these updates as follows:
- CVE-2013-2871, CVE-2013-2926, CVE-2013-2928, CVE-2013-6625, CVE-2014-1289, CVE-2014-1290, CVE-2014-1291, CVE-2014-1292, CVE-2014-1293, CVE-2014-1294, CVE-2014-1298, CVE-2014-1299, CVE-2014-1300, CVE-2014-1301, CVE-2014-1302, CVE-2014-1303, CVE-2014-1304, CVE-2014-1305, CVE-2014-1307, CVE-2014-1308, CVE-2014-1309, CVE-2014-1310, CVE-2014-1311, CVE-2014-1312, CVE-2014-1313, CVE-2014-1713 : Visiting a maliciously crafted website may lead to an unexpected application termination or arbitrary code execution. Multiple memory corruption issues existed in WebKit. These issues were addressed through improved memory handling.
- CVE-2014-1297 : An attacker running arbitary code in the WebProcess may be able to read arbitrary files despite sandbox restrictions. A logic issue existed in the handling of IPC messages from the WebProcess. This issue was addressed through additional validation of IPC messages.
Mac users running OS X Lion systems can install the Safari 6.1.3 update by choosing Apple menu > Software Update (if prompted, enter an admin password). For users running OS X Mavericks and OS X Mountain Lion systems, Safari 6.1.3 and Safari 7.0.3 may be obtained from the Mac App Store.