Another Sketchy Genieo Installer Discovered
Posted on
by
Lysa Myers
You may recall, about a month ago Genieo had posted sketchy adware installers that were posing as fake Flash alerts. Well, they’re at it again with a new variant, this time purporting to be video codecs. The behavior once installed is quite similar to the previous variant, but this version has been updated for improved compatibility with OS X 10.8.
Another hat tip to Thomas Reed for pointing out the updated variant. This new variant has slightly different behavior depending on what version of the operating system you’re running. If you try to install the file on OS X 10.8, it doesn’t ask for an admin password, as it does not yet have compatibility for its code injection components. If you try to install on 10.6 or 10.7, the installer asks for an admin password and it installs code injection components as in previous variants.
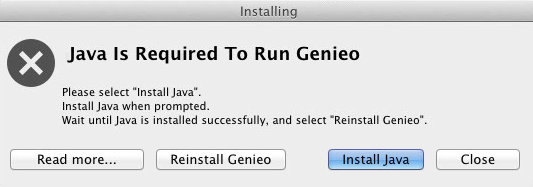
Java is required for Genieo to run, so if you have 10.7 or 10.8 without Java installed, it prompts you to install Java before proceeding.
This variant also affects the functioning of XProtect. Upon installation, it removes the Apple system quarantine flag so that the user won’t see a system alert at the first launch of the application.
As with the previous variant, this version uses a dynamic library to inject into Safari when the browser is launched. This enables it to intercept searches on Google, Bing and Yahoo and silently redirect them to Genieo or its partner engine.
Intego VirusBarrier users with up-to-date virus definitions will protect against this threat as OSX/Genieo.B. It’s advised, if you have already installed this file, to use the adware’s provided uninstaller to remove the files, as removing these files otherwise can result in system inoperability.