Another Problematic Softonic Installer Brings Adware
Posted on
by
Lysa Myers
You may recall that Softonic recently drew much ire for a short-lived but troubling installation package that surreptitiously delivered adware to people trying to install two popular applications – UnRarX and VLC. It looks like they’re at it again.
A recent blog post on The Safe Mac drew our attention to a report of a fake Flash alert that led to a fake installer download. At the time of the report, the fake alert detected OS X browsers and delivered a Genieo installation disk image:
- InstallGenieo.dmg (SHA256 44eae526f3ec2dd071cec4a1ff0d25bc8209a040739e62a0588dfabce476f1d6)
The fake alert currently delivers a Windows executable, regardless of browser version.
The Genieo and Softonic connection
Previous versions of the Genieo installer were opt-in, and the installer asked for a password. This most recent delivery method required neither and was clearly trying to trick users into thinking the installer was something other than it really was.
The Genieo application is written in Java. The application resources contain:
- Installed files dynamic libraries
- A Firefox add-on
- A Mac helper tool
- A Mac notification tool
- The Java applet
- “Partner” settings
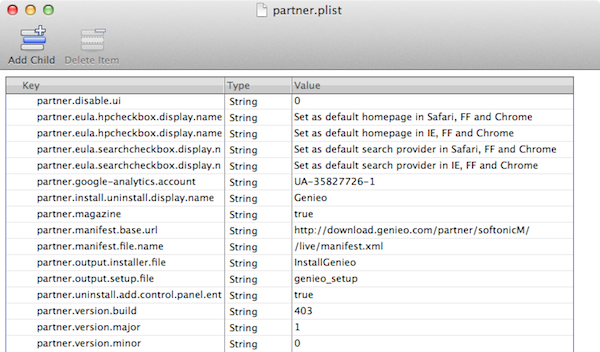
It’s within these “Partner” settings that we find some interesting information, in the most recent installer variant that’s delivered by fake alert. Within this file:
- Genieo.app/Contents/Resources/Java/Partner/genTugM/conf/partner.plist
We find this text:
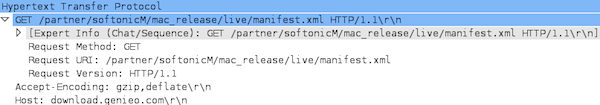
- <key>partner.manifest.base.url</key>
<string>http://download.genieo.com/partner/softonicM/</string>
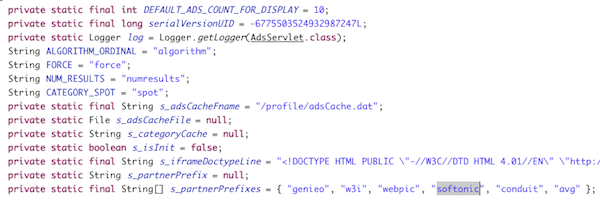
The Java applet itself also contains references to Softonic.
Running the adware in a virtual environment confirmed traffic containing references to Softonic in URLs.
This led us to the Genieo app generator for Genieo and their list of partners. While there is no explicit reference to Softonic there, but the genTugM partner installer still points to a Genieo version that contains text referencing Softonic.
The Installer in Action
Upon running the file, the installer performs a number of notable actions:
- gathering the user’s kernel mode (32 or 64 bits) and system version
- checking if Java is installed, and recommending to install it, as the Genieo application requires it
- changing browser search provider
- asking for admin privileges
- downloading Genieo.dmg
- downloading and installing third party products like Codec-M and Qtrax
- reporting installation status to analytics
Once Genieo.dmg is downloaded, it installs Genieo.app and adds it to the Login Items so that it will be restarted at login. It also installs a Launch Agent:
- /Library/LaunchAgents/com.genieo.engine.plist
Along with two dynamic libraries:
- /usr/lib/libgenkit.dylib
- /usr/lib/libgenkitsa.dylib
Libgenkit.dylib is added to OS X’s global launchd configuration file:
- /etc/launchd.conf
This dynamic library injects the second, libgenkitsa.dylib, into Safari when the browser is launched. This enables it to intercept searches on Google, Bing and Yahoo and silently redirect them to Genieo or its partner engine.
Intego VirusBarrier users with up-to-date virus definitions will detect the components of this threat as OSX/Genieo.