Adobe Updates Flash for Critical Cross-Scripting Vulnerability
Posted on
by
Peter James
Adobe has issued an out-of-band update for Flash Player to patch a vulnerability that “could be used to take actions on a user’s behalf on any website or webmail provider, if the user visits a malicious website.” Adobe says that “There are reports that this vulnerability is being exploited in the wild in active targeted attacks designed to trick the user into clicking on a malicious link delivered in an email message.”
The new version of Flash Player is 10.3.181.22. Mac users can use the plug-in’s automatic updater for the first time. If you have installed the previous version of Flash, which we wrote about here, you’ll now be able to access Flash Player preferences from the System Preferences application. Updating can occur automatically, as you can see in the Updates section of the Flash Player preferences.
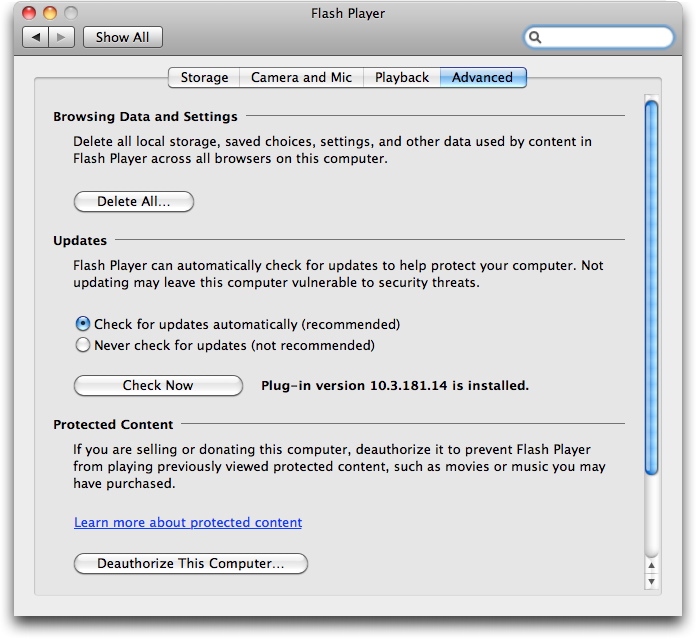
However, we are still seeing the old version of Flash Player listed. Unfortunately, the Check Now button does not do what you might expect. Other applications will open a window as they check a remote server for an update. This merely sends you to an Adobe web page which tells you the current version of Flash installed on your Mac (which you knew already, because it’s displayed in the window). There is a link to the Flash Player Download Center where you can download and install the latest version of Flash Player.
We’re planning to keep an eye on our preferences to see if and when the plug-in gets updated automatically during the day.