Adobe Patches Flash Security Flaw Under Attack in the Wild
Posted on
by
Derek Erwin
 Adobe Systems has issued a mammoth security update with patches for a combined 36 vulnerabilities, one of which is currently under attack in the wild. The most critical flaw, CVE-2015-5119, could lead to code execution. Adobe’s Flash Player updates are available for Macintosh, Windows and Linux.
Adobe Systems has issued a mammoth security update with patches for a combined 36 vulnerabilities, one of which is currently under attack in the wild. The most critical flaw, CVE-2015-5119, could lead to code execution. Adobe’s Flash Player updates are available for Macintosh, Windows and Linux.
“Adobe is aware of a report that CVE-2015-5119 is being actively exploited in the wild,” said Adobe. As noted by Lucian Constantin over at PCWorld, cybercriminals began using the exploit just a day after it was leaked from a surveillance software developer. Constantin wrote:
The exploit was found by security researchers yesterday among the 400GB worth of files stolen recently from Hacking Team, an Italian company that develops and sells intrusion and surveillance software to government agencies.
Similarly, it took just one extra day for Adobe Systems to patch the vulnerability with today’s release of Adobe Flash Player 18.0.0.203 for Mac and Windows.
Cybercriminals use Exploit Kits to attack known vulnerabilities in browser plug-ins, such as Flash Player and other Adobe software, and install malware on a victim’s computer. “These attacks are typically launched from compromised websites or through malicious advertisements,” warned Constantin.
If you’re not sure whether a popup alert claiming to be from Adobe is real or fake, take a look at our handy security tips on how to safely install and update Adobe Flash.
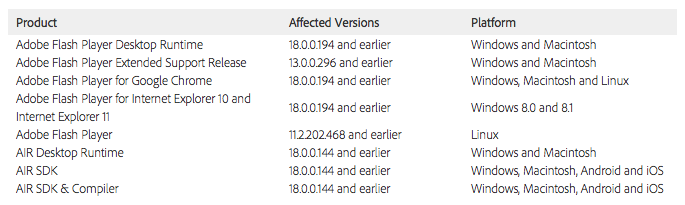
Affected software versions — which are out of date and vulnerable to attack — include the following:
Adobe’s security bulletin describes the vulnerabilities patched in these updates as follows:
- These updates improve memory address randomization of the Flash heap for the Window 7 64-bit platform (CVE-2015-3097).
- These updates resolve heap buffer overflow vulnerabilities that could lead to code execution (CVE-2015-3135, CVE-2015-4432, CVE-2015-5118).
- These updates resolve memory corruption vulnerabilities that could lead to code execution (CVE-2015-3117, CVE-2015-3123, CVE-2015-3130, CVE-2015-3133, CVE-2015-3134, CVE-2015-4431).
- These updates resolve null pointer dereference issues (CVE-2015-3126, CVE-2015-4429).
- These updates resolve a security bypass vulnerability that could lead to information disclosure (CVE-2015-3114).
- These updates resolve type confusion vulnerabilities that could lead to code execution (CVE-2015-3119, CVE-2015-3120, CVE-2015-3121, CVE-2015-3122, CVE-2015-4433).
- These updates resolve use-after-free vulnerabilities that could lead to code execution (CVE-2015-3118, CVE-2015-3124, CVE-2015-5117, CVE-2015-3127, CVE-2015-3128, CVE-2015-3129, CVE-2015-3131, CVE-2015-3132, CVE-2015-3136, CVE-2015-3137, CVE-2015-4428, CVE-2015-4430, CVE-2015-5119).
- These updates resolve vulnerabilities that could be exploited to bypass the same-origin-policy and lead to information disclosure (CVE-2014-0578, CVE-2015-3115, CVE-2015-3116, CVE-2015-3125, CVE-2015-5116).
Adobe Flash users running Mac OS X and Windows computers should update to Adobe Flash Player 18.0.0.203 (15.6 MB) immediately to avoid potential attacks. Linux users should update to Flash Player 11.2.202.481.
Flash Player for Google Chrome and Internet Explorer will be automatically updated to the latest version, and includes the security fixes mentioned here.