Adobe Issues Final 2015 Flash Player Security Update
Posted on
by
Derek Erwin
 Adobe has released security updates for Adobe Flash Player, releasing version 20.0.0.235 as its final 2015 update of the year. Flash Player 20.0.0.235 addresses “critical vulnerabilities” that could potentially allow an attacker to take control of the affected system, according to Adobe’s security bulletin (APSB15-32).
Adobe has released security updates for Adobe Flash Player, releasing version 20.0.0.235 as its final 2015 update of the year. Flash Player 20.0.0.235 addresses “critical vulnerabilities” that could potentially allow an attacker to take control of the affected system, according to Adobe’s security bulletin (APSB15-32).
Seventy-nine vulnerabilities were patched in Adobe’s final 2015 software update.
Following the update, chief technology officer at Qualys, Wolfgang Kandek, said:
“All but three of the vulnerabilitities could be used by an attacker to gain code execution running under the user in the browser. […] Flash-based attacks have been a favorite for attackers this year with many exploit kids providing very up-to-date exploits — include this in your high priority items.”
RELATED: How to Tell if Adobe Flash Player Update is Valid
Adobe software affected by these updates include the following:
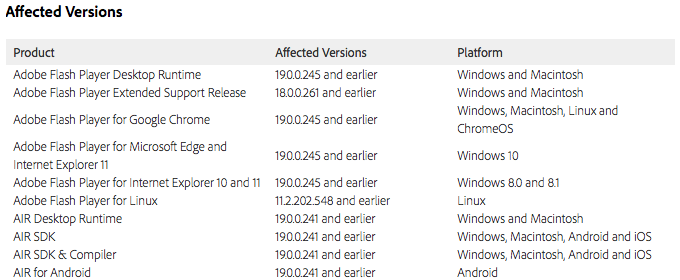
Details of the vulnerabilities addressed in this update are as follows:
- These updates resolve heap buffer overflow vulnerabilities that could lead to code execution (CVE-2015-8438, CVE-2015-8446).
- These updates resolve memory corruption vulnerabilities that could lead to code execution (CVE-2015-8444, CVE-2015-8443, CVE-2015-8417, CVE-2015-8416, CVE-2015-8451, CVE-2015-8047, CVE-2015-8455, CVE-2015-8045, CVE-2015-8418, CVE-2015-8060, CVE-2015-8419, CVE-2015-8408).
- These updates resolve security bypass vulnerabilities (CVE-2015-8453, CVE-2015-8440, CVE-2015-8409).
- These updates resolve a stack overflow vulnerability that could lead to code execution (CVE-2015-8407, CVE-2015-8457).
- These updates resolve a type confusion vulnerability that could lead to code execution (CVE-2015-8439, CVE-2015-8456).
- These updates resolve an integer overflow vulnerability that could lead to code execution (CVE-2015-8445).
- These updates resolve a buffer overflow vulnerability that could lead to code execution (CVE-2015-8415)
- These updates resolve use-after-free vulnerabilities that could lead to code execution (CVE-2015-8050, CVE-2015-8049, CVE-2015-8437, CVE-2015-8450, CVE-2015-8449, CVE-2015-8448, CVE-2015-8436, CVE-2015-8452, CVE-2015-8048, CVE-2015-8413, CVE-2015-8412, CVE-2015-8410, CVE-2015-8411, CVE-2015-8424, CVE-2015-8422, CVE-2015-8420, CVE-2015-8421, CVE-2015-8423, CVE-2015-8425, CVE-2015-8433, CVE-2015-8432, CVE-2015-8431, CVE-2015-8426, CVE-2015-8430, CVE-2015-8427, CVE-2015-8428, CVE-2015-8429, CVE-2015-8434, CVE-2015-8435, CVE-2015-8414, CVE-2015-8454, CVE-2015-8059, CVE-2015-8058, CVE-2015-8055, CVE-2015-8057, CVE-2015-8056, CVE-2015-8061, CVE-2015-8067, CVE-2015-8066, CVE-2015-8062, CVE-2015-8068, CVE-2015-8064, CVE-2015-8065, CVE-2015-8063, CVE-2015-8405, CVE-2015-8404, CVE-2015-8402, CVE-2015-8403, CVE-2015-8071, CVE-2015-8401, CVE-2015-8406, CVE-2015-8069, CVE-2015-8070, CVE-2015-8441, CVE-2015-8442, CVE-2015-8447).
Mac and Windows users running Adobe Flash Player Desktop Runtime should update to Flash Player 20.0.0.235 (16.2 MB) as soon as possible, and Linux users should update to Flash Player 11.2.202.554. Google Chrome will automatically update to the latest version, which includes Adobe Flash Player 20.0.0.228 for Windows, Mac, Linux and Chrome OS. Users of the AIR desktop runtime should update to version 20.0.0.204 by visiting the AIR download center.