The top 20 most notable Mac malware threats of 2022
Posted on
by
Joshua Long

We recently compiled our list of the top Apple security and privacy stories of 2022. Now we turn our focus specifically to the Mac malware threats of the past year. Here are all of the top malware threats that made headlines each month throughout 2022.
Note that most of the dates below relate to when these Mac malware families hit the news cycle. In a few cases, the dates indicate when Intego or other researchers discovered new variants of this malware or saw an uptick in samples or distribution attempts.
In this article:
- January 2022: SysJoker and DazzleSpy
- February 2022: CoinMiner
- March 2022: ChromeLoader and GIMMICK
- April 2022: TraderTraitor and oRAT
- May 2022: CrateDepression and Pymafka
- June 2022: Adware and more
- July 2022: “Covid” VPN Trojan and CloudMensis
- August 2022: RShell and XCSSET
- September 2022: Fake App Store Bundlore and Operation In(ter)ception
- October 2022: Alchimist framework spreads Mac malware
- November 2022: KeySteal
- December 2022: Xnspy, SentinelSneak, and ChatGPT malware
- How can I stay safe from Mac malware?
- How can I learn more?
January 2022: SysJoker and DazzleSpy
SysJoker was first written about in early January 2022, although it had actually been found in the wild in December 2021. The malware was discovered during an active attack on an educational institution’s Web server. It’s cross-platform malware, with variants designed to infect macOS, Windows, and Linux. The primary function of SysJoker appeared to have been cyberespionage, or in other words, spying on its victims. For more details, check out Intego’s SysJoker write-up.
SysJoker: Cross-Platform Backdoor Malware for Mac, Windows, and Linux
DazzleSpy was first written about in late January, but it was related to the MACMA (aka CDDS) malware campaign that Google wrote about in November 2021. This malware appeared to have been deployed by an advanced (and likely state-sponsored) threat actor with non-public knowledge of a WebKit vulnerability. DazzleSpy’s primary target appeared to have been very specific: Mac-using supporters of Hong Kong democracy. Intego wrote a detailed report about DazzleSpy in January 2022.
February 2022: CoinMiner
In late February, Luis Magisa wrote about a macOS CoinMiner sample first discovered in early January. “CoinMiner” is actually a generic name, typically used to refer to cryptocurrency-mining PUAs (potentially unwanted apps). In a typical month, Intego analyzes dozens of unique new OSX/CoinMiner samples. This particular CoinMiner sample was clearly designed with malicious intent. It used file names mimicking Adobe software, in an attempt to hide in plain sight from average users. Patrick Wardle later wrote his own technical analysis of this malware.
Other interesting malware that surfaced in February included HermeticWiper and IsaacWiper. While no Mac-specific samples were discovered, both were notable in that they were used against Ukrainian organizations immediately preceding Russia’s invasion of Ukraine. Intego wrote about HermeticWiper in late February, and later reports indicated that IsaacWiper had also been deployed around the same time.
HermeticWiper malware targeting orgs in Ukraine; here’s how to stay safe
March 2022: ChromeLoader and GIMMICK
While ChromeLoader (aka Choziosi or ChromeBack) was originally discovered in January 2022, a Mac-targeting variant first came to light in March. This variant made its way onto victims’ Macs by way of a .dmg disk image, which contained an installer that would hijack Chrome and Safari. Victims may have encountered the disk image after scanning QR codes or following links in social media posts. Several additional technical reports discussed Mac variants of ChromeLoader in April, May, and June.
The GIMMICK backdoor malware is so named because of its convoluted and unnecessarily complex design. Its discoverer, Volexity, says that GIMMICK is used in targeted attacks by Storm Cloud, a “Chinese espionage threat actor” that attacks organizations based in Asia. The Mac version was first discovered in late 2021 on an infected MacBook Pro running macOS Big Sur. GIMMICK is known to use cloud providers such as Google Drive for its command-and-control capabilities. Later in the year, Patrick Wardle wrote his own, brief technical write-up of GIMMICK.
April 2022: TraderTraitor and oRAT
In mid-April, U.S. government agencies jointly warned about state-sponsored Mac and Windows malware, dubbed TraderTraitor, that targeted blockchain companies. They attributed the malware to a North Korean-sponsored advanced persistent threat (APT) best known as Lazarus Group, and also called APT38, BlueNoroff, and Stardust Chollima. Intego previously wrote about Lazarus Group’s “Operation AppleJeus” malware campaign in 2018. TraderTraitor employs similar tactics, using Trojan horses related to cryptocurrency. This time, the malware’s primary goals are reportedly to hack the victim’s computer and spread malware on their network, steal private keys, exploit security flaws, and make fraudulent blockchain transactions. Intego detects TraderTraitor samples as OSX/Nukesped or OSX/Lazarus.
An APT group, known as Earth Berberoka or GamblingPuppet, created cross-platform malware in early 2022. Developed in the Go programming language, and with samples for Mac and Windows, oRAT was an interesting malware specimen. The Mac version was distributed via a Trojan horse masquerading as Bitget cryptocurrency software. Although multiple malware analysts wrote about oRAT in April and May, Intego had been detecting it since early March. Wardle later wrote his own oRAT analysis in October.
May 2022: CrateDepression and Pymafka
Interestingly, two presumably unrelated Mac malware campaigns surfaced in May that utilized a technique known as typosquatting. In a typosquatting attack, a malicious party registers a domain, username, or URL that’s similar to a known, legitimate one, in hopes that victims will make a typographical error and end up on their malicious page by mistake.
CrateDepression
The first to be discovered was malware known as CrateDepression. This malware relied on people seeking the trusted “rust_decimal” package to mistakenly type “rustdecimal” and download malware by mistake. The CrateDepression campaign was designed to specifically target software developers—something we’ve seen in the past, for example with the XcodeGhost campaign in 2015. More technical details about CrateDepression are available in write-ups by Juan Andrés Guerrero-Saade and Phil Stokes and Wardle.
Pymafka
Only a week after CrateDepression came to light, another site frequented by software developers—PyPI, the Python Package Index—hosted typosquatting malware. By mistyping its name, programmers looking for the legitimate PyKafka package could have accidentally stumbled upon malware distributed as “pymafka” instead (note that the K and M keys are next to each other on standard QWERTY keyboards). Pymafka, when run, would check to see which operating system it was running on (Mac, Windows, or Linux), and download a secondary malicious payload—a Cobalt Strike* Beacon that would give the malware distributor remote control over the infected computer. More technical details: Ax Sharma, Wardle.
*Note that Cobalt Strike is the name of a decade-old “adversary simulation” tool that’s sold commercially. The detection name “OSX/CobaltStrike” refers to malicious abuses of Cobalt Strike Beacons as post-exploit agents or malware droppers that are used in real-world attacks (rather than simulations).
June 2022: Adware and more
Although there weren’t any notable malware write-ups in June (other than a ChromeLoader write-up mentioned earlier), malware makers certainly didn’t take a break. In June, Intego added detection for several brand-new variants of droppers, adware, PUAs, and other malware, from families such as OSX/CobaltStrike, OSX/MaxOfferDeal (aka Genieo), and OSX/CoinMiner. Example hashes:
ade040157629be1c3c40b803c4a12be356832d99c2cd77db6efc677d1c5944d9 4dcaf4861630dae6e3c87b72fe0e53c65fb90e5128c11193bd91bd8b4d4b6e6e 6d39f593828bdf1f354396f7aaeec358292295c1d9048f4e168f14cea997014f
Each of these samples had a very low detection rate when first uploaded to VirusTotal in June. At the time, roughly 3%, 5%, or 15% of all antivirus engines apparently included detection signatures for each sample, respectively.
July 2022: “Covid” VPN Trojan and CloudMensis
“Covid” VPN Trojan
In early July, Stokes and Dinesh Devadoss wrote about their investigation of an interesting disk image, named vpn.dmg, that had been uploaded to VirusTotal on April 20. The disk image contained a Trojan horse (hence the malware’s nickname VPN Trojan) that would download a second-stage payload and establish persistence, meaning the malware would automatically run again after a reboot. An additional payload, a file named covid, would then be downloaded to the user’s home directory and then executed.
According to the researchers, the “covid” malware then phones home, attempts to detect whether it’s running inside a virtual machine (probably a weak attempt to evade malware researchers’ analysis), and creates an in-memory payload. It would then try to download an additional payload. By the time they discovered and began analyzing this malware, however, the next payload was no longer online, so the primary goals of the malware could never be fully ascertained. Wardle later wrote some additional technical observations about this malware.
Intego detects various components of this VPN Trojan as OSX/Agent, OSX/Downloader, OSX/Dldr.Agent, and OSX/Sliver.
CloudMensis, aka BaDRAT
Previously unknown backdoor malware was discovered by at least two independent research groups in April 2022. The first deep-dive report on the malware was published in July by Marc-Etienne M.Léveillé of ESET, who called it CloudMensis. It later came to light that Paul Rascagneres of Volexity was also researching the same malware at the time ESET discovered it. Rascagneres gave a presentation about the malware at a conference in September, in which he referred to it as BaDRAT (as in bad remote access Trojan). The latter believed that it may have been a macOS version of RokRAT, a Windows RAT known to be used by a threat actor known variously as InkySquid, APT37, Ricochet Chollima, ScarCruft, and Group123. This threat actor is believed to be affiliated with North Korea, as is the Lazarus Group.
Neither research team was able to identify the infection vector (i.e. how the malware would get onto an infected Mac in the first place). Both teams, however, observed that the malware attempted to leverage a number of old macOS vulnerabilities that had long since been patched, sometimes years earlier.
The malware’s capabilities are pretty standard fare for backdoor or RAT malware; it can capture screenshots, run shell commands, download and run additional malware payloads, and more. Intego detects components of this malware as OSX/CloudMensis and OSX/Adload.
August 2022: RShell and XCSSET
RShell (OSX/IronTiger)
In August, multiple security vendors independently discovered that the popular Chinese chat app MiMi had been compromised with malicious code dating back to May 26, 2022. A packed (obfuscated) string of JavaScript code was added to the app that downloaded and ran a reverse-shell (backdoor) app with the filename rshell. Both research groups found this malware while researching a server hosting a sample of HyperBro, a Windows malware family.
Based on its filename, the malware specimen is often called RShell (with various capitalization, including Rshell and rShell). Intego, however, detects this malware as OSX/IronTiger. Iron Tiger is one of many nicknames for the APT group associated with this malware campaign; the group is also called LuckyMouse, Emissary Panda, APT27, and Bronze Union by various security vendors.
SEKOIA.IO was the first to publish a write-up on the malware, initially to its clientele on August 10, and then publicly on August 12, the same day as Daniel Lunghi and Jaromir Horejsi reported on it.
New XCSSET variant
Also in August, Stokes and Devadoss wrote about a new version of XCSSET that had been seen active from April to August 2022. Intego previously covered XCSSET when it first emerged two years earlier, in August 2020.
One notable change over the years is that, while XCSSET was originally distributed via infected Xcode projects (i.e. targeting developers), it switched to a fake Mail app in 2021 and a fake Notes app in 2022, according to Stokes and Devadoss. Interestingly, XCSSET makes heavy use of AppleScripts with embedded shell scripts.
September 2022: Fake App Store Bundlore and Operation In(ter)ception
Poisoned search results lead to fake App Store pages, Bundlore malware
In September, Intego researched search engine poisoning campaigns, some of which led to fake App Store pages and OSX/Bundlore malware downloads. Bundlore (also called Bnodlero) is a nearly decade-old malware family. It’s commonly associated with adware dropper malware, although it sometimes may have additional capabilities. Bundlore typically infects Macs via Trojan horses masquerading as legitimate Mac software. For more details on this malware campaign, see Fake App Store pages are the new fake Flash Player alerts.
Lazarus Group resurfaces with Operation In(ter)ception
As if TraitorTrader in April wasn’t enough for one year, the threat actor Lazarus Group launched another Mac-targeted campaign just months later. ESET Research tweeted a thread about signed Mac malware that disguised itself as a job description document from Coinbase, a cryptocurrency company. The malware bundle appeared to have been code-signed on July 21, and was uploaded to VirusTotal on August 11. But that’s not where the story ends.
#ESETresearch #BREAKING A signed Mac executable disguised as a job description for Coinbase was uploaded to VirusTotal from Brazil 🇧🇷. This is an instance of Operation In(ter)ception by #Lazarus for Mac. @pkalnai @dbreitenbacher 1/7 pic.twitter.com/dXg89el5VT
— ESET Research (@ESETresearch) August 16, 2022
Devadoss and Stokes, researchers at SentinelOne, wrote in September about their own deep dive into a closely related malware campaign, which they called Operation In(ter)ception. Their analysis explored a similar job description PDF, this time for a position at Crypto.com, and how it was used as a decoy to install malware and gain persistence (i.e. how the malware runs itself again after the Mac reboots).
As with TraderTraitor, Intego detects Operation In(ter)ception malware as OSX/Nukesped.
October 2022: Alchimist framework spreads Mac malware
In October, details about a new Chinese-language attack framework came to light. The framework’s creators call it Alchimist, and its associated remote access Trojan (RAT) is called Insekt. The Alchimist framework is designed to target macOS, Windows, and Linux. At the time, Insekt payloads were compiled to run on Windows and Linux specifically, although a Mac-compatible backdoor was also found amongst Alchimist’s tools.
Oddly, Alchimist was also discovered alongside Mac dropper malware designed to exploit a 2021 vulnerability—one that only affects command-line software that isn’t included with macOS. For more details, check out Intego’s report about Alchimist and Insekt malware.
Malware Attack Framework “Alchimist” Designed to Exploit Macs
Not Malware: Fake Alert Pop-Ups
It’s worth noting that Intego saw an increase in the number of users reporting fake-alert browser pop-ups in October. These were simple JavaScript-invoked dialog boxes that claimed, for example:
- “Safari – Alert” / “Suspicious Activity Might Have Been Detected.”
- “Major Security Issue” / “To fix it please call Support for Apple”
- [Fake FBI URL] / “YOUR BROWSER HAS BEEN LOCKED.”
- “ALL PC DATA WILL BE DETAINED AND CRIMINAL PROCEDURES WILL BE INITIATED AGAINST YOU IF THE FINE WILL NOT BE PAID.”
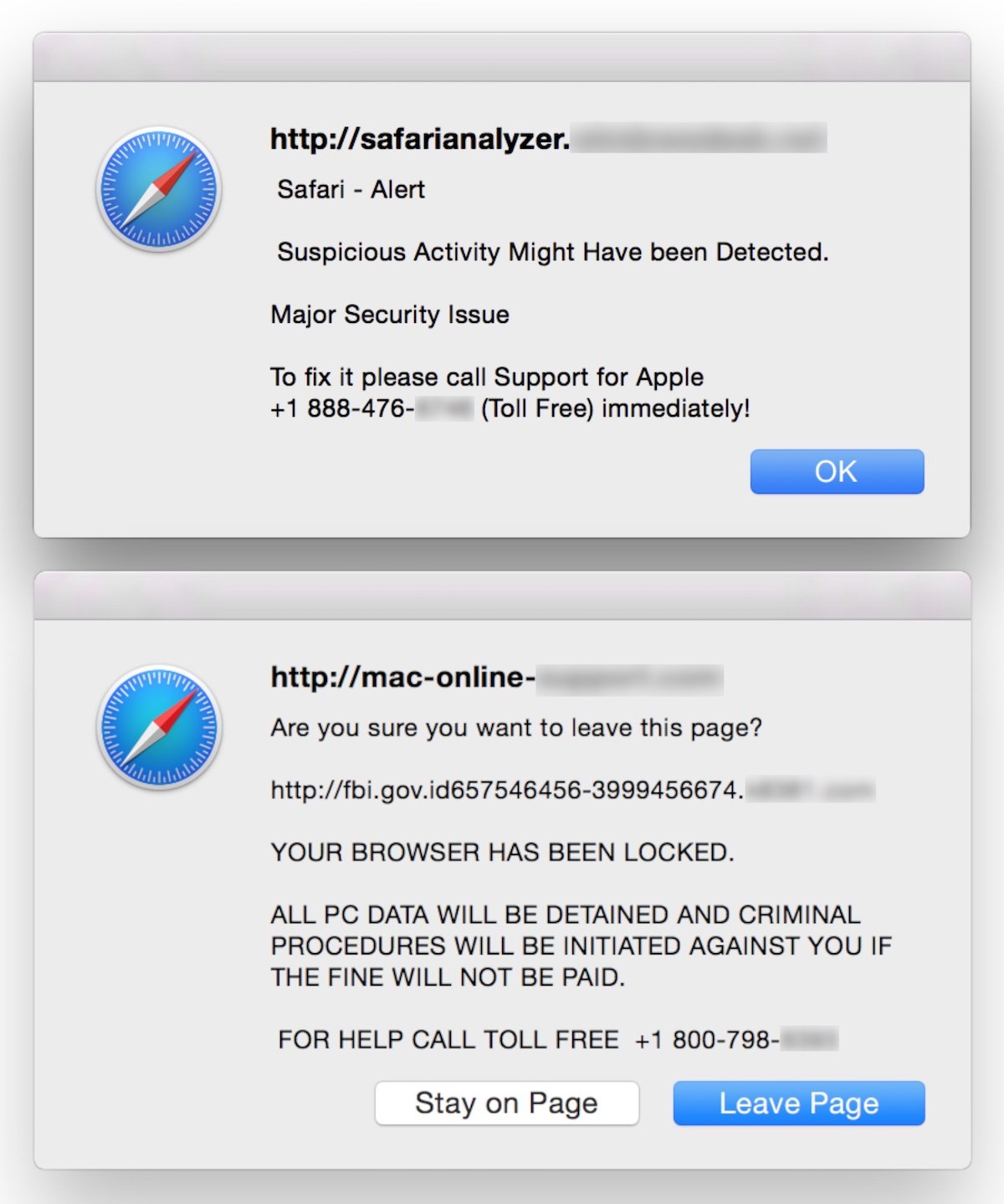
In some cases, the messages would be read aloud to users via text-to-speech, which can be very frightening if unexpected.
Users who saw (or heard) these messages were concerned about possible malware infections on their Macs. However, these messages were in fact fraudulent alerts from sites operated by scammers. Most users who ended up on these sites were likely led there by malicious results in search engines, or possibly by mistyping a domain in the browser’s address bar and getting redirected to a scam site. Closing the browser window, or quitting the browser, is typically all it takes to escape from such scam sites.
The issue was so prevalent in October that, in order to more easily handle the influx of support calls, and to help those searching for answers, Intego created a guide on our support site. Here’s how to deal with the (non-malware) Web browser pop-up alert scam.
November 2022: KeySteal
In November, Luis Magisa and Qi Sun wrote about a Trojanized installer for ResignTool, a macOS app used by iOS and iPadOS software developers. The malicious installer package, generically named archive.pkg, then grabs the victim’s macOS Keychains and exfiltrates them to an attacker-controlled server.
As this KeySteal Trojan installer was found on VirusTotal, it’s unclear whether or not the malware had been used against any targets in the wild. Wardle’s later write-up brought to light several additional tidbits. The installer package had been uploaded to VirusTotal twice in October, just a day apart from each other, evidently from two different countries: Singapore and Egypt. While the malicious installer package was once code-signed with a developer certificate obtained from Apple, at some point Apple revoked the certificate; it’s not clear exactly when Apple did so, however.
Intego detects this malware as OSX/KeySteal. Other vendors may detect it as KCSteal or other names.
December 2022: Xnspy, SentinelSneak, and ChatGPT malware
Xnspy: commercial iOS spyware
On episode 271 of The Intego Mac Podcast, we discussed commercial spyware for iOS, including Xnspy. This category of malware, also available for Android, is often referred to as “stalkerware.” It’s typically marketed toward people who may want to (for example) keep tabs on a significant other they suspect of cheating. Thus, the malware is intentionally designed to hide from the victim and secretively report back to the stalker who installed it. A pair of researchers, Vangelis Stykas and Felipe Solferini, spent months analyzing several stalkerware apps and presented some of their findings at a security conference in December.
SentinelSneak
On December 19, Karlo Zanki wrote about SentinelSneak, a Trojan horse masquerading as software related to security firm SentinelOne. Several variants of the malware were uploaded to PyPI in the weeks leading up to the report. It seems that the malware maker attempted to infect victims via a typosquatting-like attack; the malware’s PyPI package name was SentinelOne, while a preexisting (non-malicious) package was named SentinelOne4py. The malware, written in the Python programming language, is designed to infect both macOS and Linux systems.
Shlayer
Malware researcher Taha Karim wrote an analysis of a Shlayer variant in late December, although this particular variant actually originated back in 2021. It’s still an interesting write-up, as it details some of the ways Shlayer has evolved in recent years. Intego was the first to discover and write about Shlayer in February 2018.
ChatGPT malware
On December 29, a user created a new thread on a hacker forum claiming that they had successfully created new variants of existing Python-language malware, with the help of a new artificial intelligence bot. It later came to light that another forum user, who had posted on December 21, used the same technology to help write ransomware in Python and an obfuscated downloader in Java. On December 31, a third user bragged that they had abused the same AI to “create Dark Web Marketplace scripts.” All three forum users apparently used ChatGPT, an AI bot that became publicly available on November 30.
The original report did not specify whether any of the generated malware code could be used against Macs, but it’s plausible. Until early 2022, macOS did, by default, include the ability to run Python scripts. Even today, many developers and corporations install Python on their Macs.
ChatGPT is programmed with “safety mitigations” to avoid answering questions that appear to have malicious intent. However, in its current form, the AI seems oblivious to the motives of users who make requests involving code that can potentially be used for malicious purposes. (See our article, “ChatGPT is malware makers’ new A.I. partner in crime.”) We can expect to see more malware re-engineered or co-designed by AI in 2023 and beyond.
How can I stay safe from Mac malware?
 Intego VirusBarrier X9, included with Intego’s Mac Premium Bundle X9, can protect against, detect, and eliminate all of the malware covered in this write-up, and a lot more.
Intego VirusBarrier X9, included with Intego’s Mac Premium Bundle X9, can protect against, detect, and eliminate all of the malware covered in this write-up, and a lot more.
If you believe your Mac may be infected, or to prevent future infections, it’s best to use antivirus software from a trusted Mac developer. VirusBarrier is award-winning antivirus software, designed by Mac security experts, that includes real-time protection. It runs natively on both Intel- and Apple silicon-based Macs, and it’s compatible with Apple’s current Mac operating system, macOS Ventura.
If you use a Windows PC, Intego Antivirus for Windows can keep your computer protected from malware.
How can I learn more?
Be sure to check out our previous article covering some of the top Apple-related security and privacy news from 2022.
We’ve also previously covered some highlights of Apple malware from 1982 to 2020.
Key Moments in the History of Mac Malware – 1982 to the Present
For additional overviews of the Mac malware of 2022, you can refer to write-ups by Patrick Wardle of Objective-See, Phil Stokes of SentinelOne, and SecureMac.
 Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
Each week on the Intego Mac Podcast, Intego’s Mac security experts discuss the latest Apple news, including security and privacy stories, and offer practical advice on getting the most out of your Apple devices. Be sure to follow the podcast to make sure you don’t miss any episodes.
You can also subscribe to our e-mail newsletter and keep an eye here on The Mac Security Blog for the latest Apple security and privacy news. And don’t forget to follow Intego on your favorite social media channels: ![]()
![]()
![]()
![]()
![]()
![]()
![]()