More on OSX/Crisis —Advanced Spy Tool
Posted on
by
Lysa Myers
Yesterday we discussed new malware for OS X called OSX/Crisis, which is a brand new Trojan that installs a backdoor on infected machines. Here we’ll discuss some new details that have been uncovered, including some files that are a possible installer for the files found yesterday.
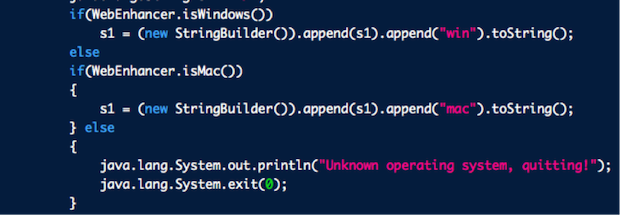
It appears one possible installation mechanism for the OSX/Crisis malware has been found. It arrives as a Java applet with one of a couple possible names and relies on social engineering to get people to activate the installer. If it’s run, the applet will check to see whether it’s being run on Windows or OS X. If it is being run on OS X, it will continue the infection chain we detailed yesterday (basically it entails installing silently to open a backdoor that’s hidden by a rootkit, then phoning home for commands) .
This Java applet technique has been a popular one for multi-platform infection, as Java will work on all common operating systems. Java has not, however, been installed by default on OS X from 10.7 on. This means it is unlikely that a Java applet is the only method of installation.
So far these are the two different filenames we’ve seen for installing OSX/Crisis:
- adobe.jar
- AdobeFlashPlayer.jar
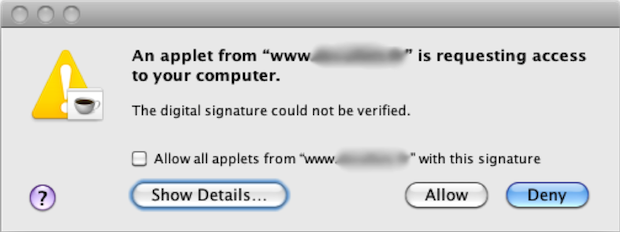
These filenames definitely seem to be pointing towards a focus on gaining the user’s trust. Below is an image of the alert the user sees when the Java Applet runs, requesting user permission to install:
Once the backdoor is installed, it patches several applications to spy on an infected user’s activities when they use those programs:
- Adium
- Skype
- Microsoft Messenger
- Firefox
It also patches the Activity Monitor to hide itself from the user, so that they will be less likely to try to remove the malware.
This malware allows the person operating it to do some rather impressive functions:
- Spying on Skype audio traffic and recording all conversations and phone calls
- Spying on Safari or Firefox browsers to record URLs and screenshots
- Recording IM messages in both MS Messenger and Adium
- Sending file contents to the control server
Upon further inspection of this threat, it appears there may be another strange detail about this malware that is worth noting: There are sections of code that point to this being part of a commercial malware package that is sold mostly in the US and Europe.
The company that created the malware package is called Remote Control System DaVinci, which is apparently a play on the owner’s name and possibly a reference to the movie Hackers. They gear their product towards government surveillance, though they have also apparently sold it to several banks and at least one other commercial company. Due to the cost (€200,000), this product is unlikely to be used by your average script kiddy in his parents’ basement.
From a technical perspective, this is a very advanced and fully functional threat. Due to the apparent cost of this malware package, it’s unlikely that this will be more than a targeted attack. But if you are the intended target, it’s very important that you have good security measures. Most vendors now have protection for the known components, but it’s unlikely that this is the last version of this malware (or its installation packages) that we will see.