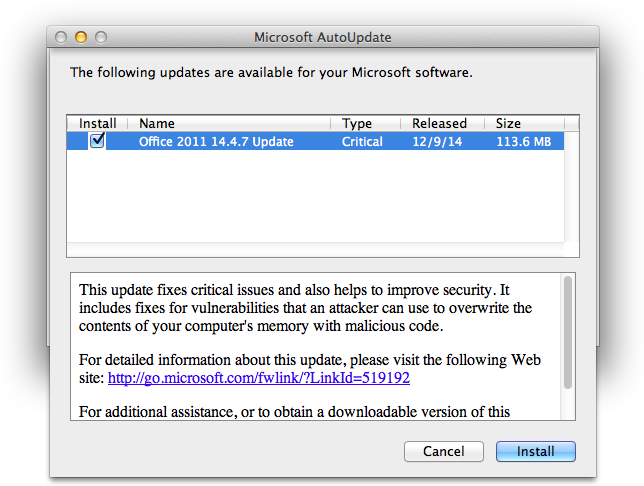
Microsoft Office 2011 14.4.7 Update Patches Critical Vulnerability
Posted on
by
Derek Erwin
Microsoft has released Office 2011 14.4.7 Update for Mac OS X version 10.5.8 or later. These updates improve the security of Microsoft software with fixes for a vulnerability that an attacker can use to overwrite the contents of an affected computer’s memory with malicious code.
The Office for Mac update applies to the following Microsoft software: Office 2011, Office 2011 Home and Business Edition, Word 2011, Excel 2011, PowerPoint 2011, Outlook 2011, Office for Mac Standard 2011 Edition, Microsoft Office for Mac Home & Student 2011, and Microsoft Office for Mac Academic 2011.
Office 2011 14.4.7 Update patches the following vulnerability:
CVE-2014-6357 : Use-after-free vulnerability in Microsoft Office 2010 SP2, Office 2013 Gold and SP1, Office 2013 RT Gold and SP1, Office for Mac 2011, Word Viewer, Office Compatibility Pack SP3, Word Automation Services on SharePoint Server 2010 SP2 and 2013 Gold and SP1, and Office Web Apps 2010 SP2 and 2013 Gold and SP1 allows remote attackers to execute arbitrary code via a crafted Office document, aka “Use After Free Word Remote Code Execution Vulnerability.”
Microsoft further explained that exploitation of CVE-2014-6357 requires that a user opens a specially crafted file with an affected version of Microsoft Office software. There are multiple attack scenarios, as outlined by Microsoft’s security bulletin:
- In an email attack scenario, an attacker could exploit the vulnerability by sending a specially crafted file to the user and by convincing the user to open the file in an affected version of Microsoft Office software.
- In a web-based attack scenario, an attacker could host a website that contains a file that is used to attempt to exploit the vulnerability.
- Compromised websites and websites that accept or host user-provided content could contain specially crafted content that could exploit this vulnerability.
In the third scenario above, however, Microsoft clarified how an attacker might trick Mac users into visiting compromised websites:
An attacker would have no way to force users to visit a specially crafted website. Instead, an attacker would have to convince them to visit the website, typically by getting them to click a link in an email message or Instant Messenger message that takes them to the attacker’s site, and then convince them to open the specially crafted file in an affected version of Microsoft Office software.
Microsoft’s Office for Mac update addresses the vulnerability by correcting the way that Microsoft Word parses specially crafted files.
We strongly encourage all users running Microsoft Office 2011 for Mac apply these updates as soon as possible. Mac users can update your software by using Microsoft’s AutoUpdate application, or you can visit Microsoft Download Center to get the Office 2011 14.4.7 Update (113.6 MB).