Hacker Claims to Have Discovered Undocumented iOS “Backdoor”; Apple Denies NSA Collusion
Posted on
by
Graham Cluley
 A data forensics expert and jailbreaker has discovered what he claims to be a undocumented “backdoor” in the iOS operating system used on iPhones and iPads that could be exploited by the NSA and other law enforcement agencies.
A data forensics expert and jailbreaker has discovered what he claims to be a undocumented “backdoor” in the iOS operating system used on iPhones and iPads that could be exploited by the NSA and other law enforcement agencies.
Jonathan Zdziarski (also known as “NerveGas”) presented his findings this month at the annual Hackers on Planet Earth (HOPE X) conference in New York.
The talk, entitled “Identifying Backdoors, Attack Points, and Surveillance Mechanisms in iOS Devices,” claimed that the undocumented functions could be used by unauthorised parties to wirelessly extract sensitive data from iOS devices, without requiring a password or PIN.
The news has, understandably, generated a lot of scary headlines—but it appears that exploitation of the so-called “backdoor” may be far from trivial.
Firstly, the iPhone or iPad you wish to extract data from needs to have been paired with a regular desktop or laptop computer via USB. At that point, your mobile device and your computer create a secure encrypted SSL channel to exchange information, by exchanging certificates and encryption keys.
 The pairing data is stored on your mobile device and computer, and is normally never wiped unless you perform a factory reset.
The pairing data is stored on your mobile device and computer, and is normally never wiped unless you perform a factory reset.
If an unauthorised party could get hold of that pairing information, then—argues Zdziarksi—they could begin an attack.
So, how could they access the pairing data? Well, one way might be to install spyware onto the targeted user’s desktop or laptop computer.
But bear this in mind: if your computer has already been compromised by malware, haven’t you already got a heap load of problems, aside from the possibility that your Apple iPhone may also come under attack?
After all, a compromised MacBook which has a malware infection could log your passwords as you type them on the device, steal information from your computer and access your online accounts relatively easily.
Chances are that that would be a more than satisfactory result for the typical data thief.
But to also access the data on a paired iPhone or iPad, a malicious hacker would have to go further. For instance, they could create a bogus hotspot using a WiFi network name that has been previously used by the mobile device, allowing it to connect and scoop up sensitive data.
Zdziarski’s presentation at HOPE X asked the following questions of Apple:
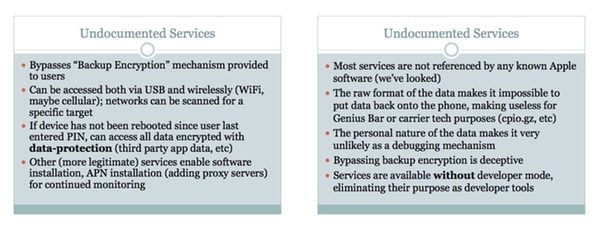
- Why is there a packet sniffer running on 600 million personal iOS devices instead of moved to the developer mount?
- Why are there undocumented services that bypass user backup encryption that dump mass amounts of personal data from the phone?
- Why is most of my user data still not encrypted with the PIN or passphrase, enabling the invasion of my personal privacy by YOU?
- Why is there still no mechanism to review the devices my iPhone is paired with, so i can delete ones that don’t belong?
Apple clearly didn’t want to get into a detailed and public tit-for-tat conversation with Zdziarski regarding his accusations, but it did defend itself, strongly denying any suggestion that it had assisted the likes of the NSA by sneakily incorporating a backdoor into the iOS code.
Instead, the company claims, iOS collects diagnostic and troubleshooting information for use by developers and enterprise users:
We have designed iOS so that its diagnostic functions do not compromise user privacy and security, but still provides needed information to enterprise IT departments, developers and Apple for troubleshooting technical issues. A user must have unlocked their device and agreed to trust another computer before that computer is able to access this limited diagnostic data. The user must agree to share this information, and data is never transferred without their consent.
As we have said before, Apple has never worked with any government agency from any country to create a backdoor in any of our products of services.
In a blog post published after his HOPE X talk, Zdziarski played down conspiratorial theories:
“I am not suggesting some grand conspiracy. There are, however, some services running in iOS that shouldn’t be there, that were intentionally added by Apple as part of the firmware and that bypass backup encryption while copying more of your personal data than ever should come off the phone for the average consumer.”
“My hope is that Apple will correct the problem. Nothing less, nothing more. I want these services off my phone. They don’t belong there.”
To be honest, what Zdziarski describes doesn’t feel like much of a backdoor to me. It’s not some secret method that Apple’s developers built into the iOS operating system to give them easy access later.
If anything, it’s a potential point of weakness that a suitably resourced group might be able to exploit to gather private information against the wishes of the targeted user.
Of course, that doesn’t mean that Apple shouldn’t do everything in its power to reduce the chances of that ever happening.
Whether Apple will change the iOS code in light of Zdziarski’s revelations remains to be seen. But if they do not address it, one has to wonder, why not?
Do you think Apple has acted suspiciously? Do you think the accusations of a backdoor are overblown? Leave a comment below with your opinion.