1,500 Apple-Approved iOS Apps at Risk From Data-Exposing Vulnerability
Posted on
by
Graham Cluley

There’s something rotten in the state of Apple security.
In recent weeks the company has seen its products bedevilled with security flaws, said it’s too hard to patch users running vulnerable, older versions of its software, and when it has released a security patch for at least some of its at-risk users—seen it fail abysmally to protect against the problem it was supposed to defend.
Meanwhile, against this backdrop, Cupertino has been banning legitimate anti-virus apps from the iOS app store—apparently on a whim.
Can things get worse?
Well, apparently they can.
Now news reaches us that some 1,500 approved apps in the so-called “walled garden,” famously vetted vigorously by Apple, have been found to contain a serious vulnerability that could be exploited by hackers to spy on communications, steal passwords and bank account information.
The problem, according to a blog post by security analytics firm SourceDNA, lies in AFNetworking, a popular open-source library used by developers to give their apps networking capabilities.
Unfortunately, a version (2.5.1) of AFNetworking was released in January that contained a serious vulnerability that could allow malicious hackers to launch man-in-the-middle attacks, busting wide open HTTPS/SSL traffic for interception.
In other words, if you have an app on your iPad or iPhone that uses AFNetworking 2.5.1, any communications you make using that app—including your passwords or private conversations—could be stolen.
AFNetworking was patched in late March, but that’s no good to you if the at-risk apps you are running on your iOS device have not been recompiled using the new fixed version of the library.
Even if you have updated at-risk apps since AFNetworking was fixed in late March, that’s no guarantee that the apps on your smartphone are now secure and—of course—there’s no way to be 100% certain that anything you did with vulnerable apps since January might not have fallen into the hands of hackers.
So, you probably have some questions…
What apps are vulnerable?
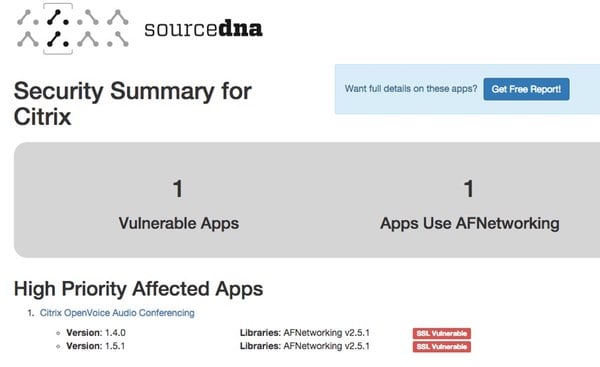
SourceDNA says that some apps from big name companies were affected, including Yahoo, Microsoft, Uber, and Citrix. However, no definitive list of affected apps has yet been released in an attempt to avoid real-life attacks.
It’s also worth bearing in mind that any list is likely to change, as app developers produce new versions including the fixed AFNetworking library.
So how am I supposed to tell if I’m at risk?
SourceDNA has produced an online search facility where you can enter an app vendor, and find out whether their product is vulnerable and if a fixed version has been released.
If I have a vulnerable app on my iPhone or iPad, does that mean that the entire device is exposed?
Not at all. This isn’t a problem with iOS. This is a problem with a code library which might be in some of your apps. Only activity you have inside those apps might be at risk. Which is something, I suppose.
I thought Apple was supposed to be really rigorous about vetting apps, and meant to stop apps that might endanger me from getting into the App Store?
Yes, you thought correctly. In this instance, they failed. In their defence, their current testing methodology might not be extensive enough to pick up these kind of flaws.
So what is Apple going to do about it?
What would you like them to do?
How about they remotely remove any vulnerable apps from users’ iPhones and iPads?
Ahh. The nuclear option.
Well, yes. They could do that, and it could be argued that from the security and privacy point of view that might be the correct course of action. However, it sure sounds inconvenient and would probably cause an uproar amongst users.
Okay, well how about they remove vulnerable apps from the App Store until fixed versions are available?
Again, that might be an option. But I can still see how that may prove unpopular with both users and app developers—some of whom might say they’re not concerned about the theoretical risk and are happy to take their chances until a fixed version of the app is available.
Hmm. Shouldn’t Apple simply stop vulnerable apps getting into the App Store in the first place?
I’m with you there! That would be nice, wouldn’t it? But it’s not really possible to do that with 100% precision – and delays in vetting would no doubt cause unrest amongst developers and users too.
Surely there’s something else that could be done to protect users from risks like this? Couldn’t you run a scanner to see if you have a dodgy app or security problem on your device?
You mean a bit like anti-virus software does on your Mac or PC? Yes, that might be a good idea for iPads and iPhones too. After all, that’s what you can do on Android which, to be fair, suffers much more from malicious attacks than iOS.
But, there’s a problem.
What’s that?
Apple doesn’t very much like the idea of anti-virus vendors writing products for iOS. In fact, it bans even ones with basic functionality from the App Store—let alone the kind of sophisticated functionality that security firms would love to build into them.
Like I said, something is rotten in the state of Apple security.