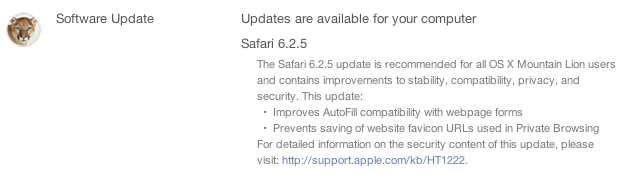
Apple’s Safari 8.0.5, Safari 7.1.5, and Safari 6.2.5 Updates Fix Privacy Flaws
Posted on
by
Derek Erwin

Apple has updated its web browser with fixes for multiple privacy flaws, releasing Safari 8.0.5, Safari 7.1.5, and Safari 6.2.5 for Yosemite, Mavericks, and Mountain Lion. These updates mitigate a total of ten vulnerabilities (CVEs), including several web browsing privacy related flaws and a number security issues related to arbitrary code execution.
The new Safari web browser is available for: OS X Mountain Lion 10.8.5, OS X Mavericks 10.9.5, and OS X Yosemite 10.10 to 10.10.2.
The Safari 8.0.5, 7.1.5, and 6.2.5 security updates tackle the following vulnerabilities, according to Apple’s security notice:
- CVE-2015-1129 : Users may be tracked by malicious websites using client certificates. An issue existed in Safari’s client certificate matching for SSL authentication. This issue was addressed by improved matching of valid client certificates.
- CVE-2015-1128 : Notifications preferences may reveal users’ browsing history in private browsing mode. Responding to push notification requests in private browsing mode revealed users’ browsing history. This issue was addressed by disabling push notification prompts in private browsing mode.
- CVE-2015-1112 : Users’ browsing history may not be completely purged. A state management issue existed in Safari that resulted in users’ browsing history not being purged from history.plist. This issue was addressed by improved state management.
- CVE-2015-1119, CVE-2015-1120, CVE-2015-1121, CVE-2015-1122, CVE-2015-1124 : Visiting a maliciously crafted website may lead to an unexpected application termination or arbitrary code execution. Multiple memory corruption issues existed in WebKit. These issues were addressed through improved memory handling.
- CVE-2015-1127 : Users’ browsing history in private mode may be indexed. A state management issue existed in Safari that inadvertently indexed users’ browsing history when in private browsing mode. This issue was addressed by improved state management.
- CVE-2015-1126 : Visiting a maliciously crafted website may lead to resources of another origin being accessed. An issue existed in WebKit’s credential handling for FTP URLs. This issue was addressed by improved URL decoding.
Mac users can install the updated Safari web browser by choosing Apple menu > Software Update (if prompted, enter an admin password), or the updates may be obtained from the Mac App Store.