Apple Safari Now Offers Per-Site Java Enabling
Posted on
by
Joshua Long
On Tuesday, Apple released two new Java-related security updates: an update for Java SE 6 and an update for supported Mac versions of Safari. The Java SE update, available for Mac OS X Snow Leopard v10.6.8 and later versions of OS X with Java SE 6 installed, patches vulnerabilities that Oracle patched for other platforms in Java 6 Update 45 and Java 7 Update 21, which were also released on Tuesday.
This update appears either in Software Update or the Mac App Store as “Java for OS X 2013-003” for Lion and Mountain Lion users, and it appears in Software Update as “Java for Mac OS X 10.6 Update 15” for Snow Leopard users.
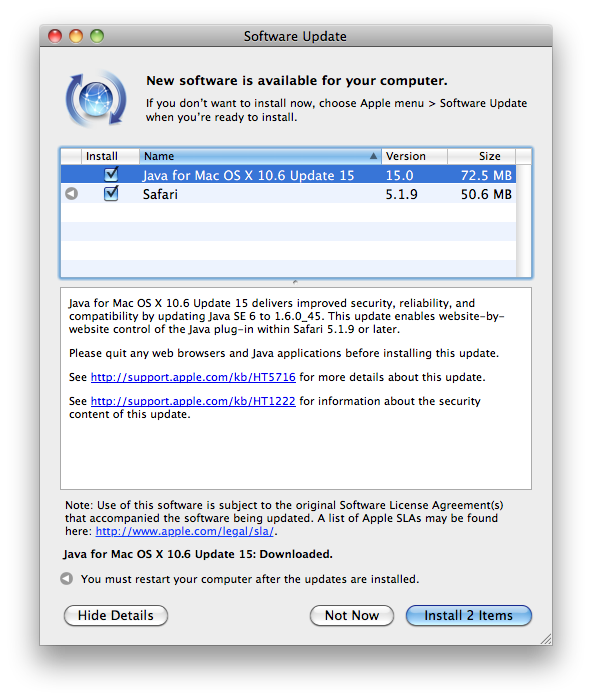
Beginning with Java SE 7, Apple no longer releases its own separate versions of Java updates. Users of OS X Lion or Mountain Lion with Java SE 7 installed will need to obtain Java 7 Update 21 from Oracle’s Java SE Downloads page.
Meanwhile, Apple also released Safari 6.0.4 for Mountain Lion and Lion, as well as Safari 5.1.9 for Snow Leopard. The new versions of Safari give users more granular control over which sites may run Java applets. If Java is enabled, the next time a site containing a Java applet is visited, the user will be asked whether or not to allow the applet to load, with buttons labeled Block and Allow:
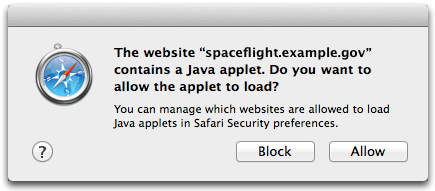
(As an aside, does this Block-or-Allow dialog box remind anyone else of a certain “Get a Mac” ad?)
The new versions of Safari now have a “Manage Website Settings…” button next to the Allow Java setting in Safari’s Security preferences:
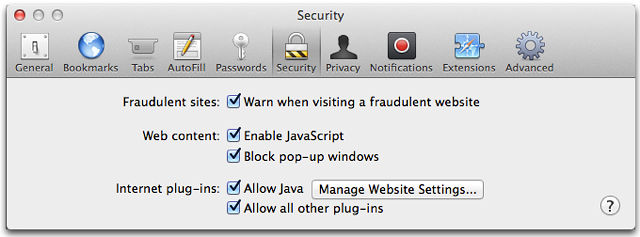
Clicking on “Manage Website Settings…” will bring up a new dialog box displaying each site that has contained an embedded Java applet since the new version of Safari was installed. Users may select any of four levels of Java access for a given site: Ask Before Using, Block Always, Allow, and Allow Always.
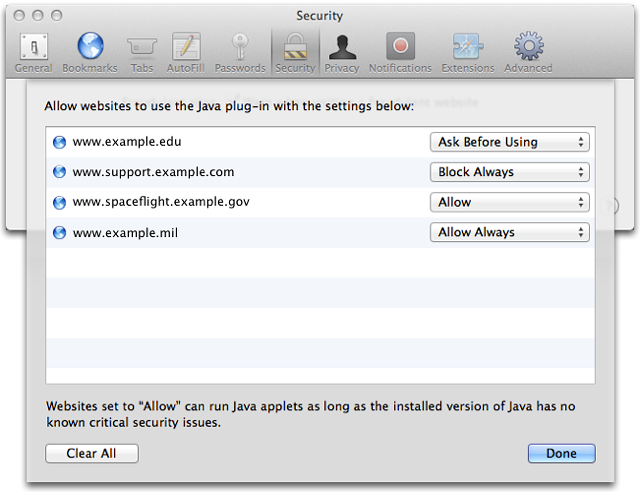
Ask Before Using displays the Block-or-Allow dialog box every time a page on the site tries to load a Java applet.
Block Always displays the text “Blocked Plug-in” anywhere a Java applet would have appeared on the site.
Allow obviously allows the site to run Java applets, but this setting also permits Safari to notify a user if a newer version of Java is available and prompt the user to download it before proceeding to the site. (Ask Before Using also notifies users about available Java updates.) Presumably this takes advantage of the Java version strings in XProtect.meta.plist, a feature of Apple’s Safe Downloads List that we’ve mentioned previously.
Always Allow is the same as Allow except that doesn’t prompt the user first if a newer version of Java is available. Apple recommends only using this setting for highly trusted sites (for example, sites on one’s corporate intranet).
Of course, if you already know you don’t need Java running in your browser at all, or if you’re not sure whether you need it, the safest option is still to ensure that Allow Java is unchecked in Safari’s Security preferences (click on the Safari menu, then click on Preferences…, and then click on Security). If you later discover that you need Java enabled for a particular site, you can enable Java and then just allow Java for that site only.
Users of Safari for Windows are still stuck at version 5.1.7. In case you missed it, Apple silently released Safari 5.1.8 for Snow Leopard after a several–month hiatus from Snow Leopard Safari security updates. Apple did not release a corresponding Windows Safari update at that time, either.
UPDATE: Another interesting side note: Oracle was supposed to have stopped releasing Java 6 security updates in February, but has continued to release security updates for it since then.
Safari screenshots courtesy of Apple.