Security & Privacy + Security News
Apple Rolls Out OS X Patch to Protect Against Critical NTP Security Flaw
Posted on
by
Graham Cluley

Just when you imagined it was safe to relax for the holidays, another serious bug is found on the internet.
Google security researchers discovered a critical security hole in the network time protocol (NTP), used by Unix-based systems such as OS X to synchronise computer clocks.
The vulnerabilities in NTP, which can be exploited remotely, could allow a hacker to take remote control of your computer.
Fortunately, Apple has released a patch.
In fact, the company is telling the media that it has pushed out its first-ever “seamless” security update, fully automated without any user interaction required.
Indeed, when I started my iMac on Tuesday morning I saw a screen like the following captured by Andrew Cunningham of Ars Technica.
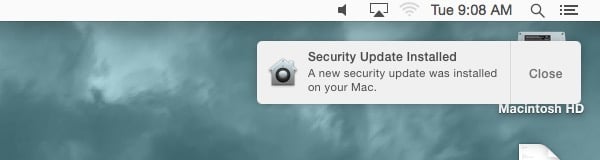
At the time the unexpected message made me raise my eyebrows. After all, it said “Security update” but didn’t tell me *what* security update, or where I might find more information should I be interested in what had changed on my computer. I like to know what’s happening on my Mac and not be left in the dark.
Only when I Google’d was I able to find out that I had been the recipient of an automatic security update from Apple, and breathed a sigh of relief that it had passed without incident.
That, after all, is how you want security updates to work. There have been too many incidents in the past where updates have gone wrong (especially on the Microsoft Windows platform, although Apple isn’t immune either) and required some quick backtracking.
What’s odd is that when I then turned on my laptop, an Apple MacBook Air, I saw no message that it had received an automatic security update. In fact, I waited half an hour or so for the comforting message to pop up. But nada.
I even went to check the App Store preferences on my laptop (available via System Preferences / App Store) to see if I had configured them to automatically download security updates that Apple pushed out.
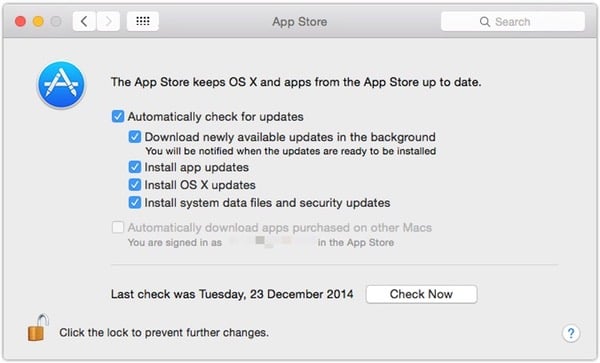
I couldn’t see any obvious settings there which might have been preventing my MacBook from receiving the super-critical NTP patch.
So, eventually, I checked manually for a security update via App Store / Updates. And sure enough it was there – with an explanation of what the security patch was for, and a bolded message telling me to install it as soon as possible.
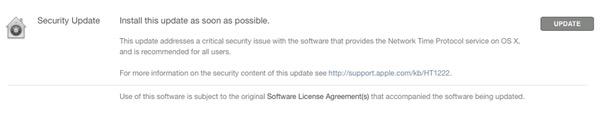
Security Update
Install this update as soon as possible
This update addresses a critical security issue with the software that provides the Network Time Protocol service on OS X, and is recommended for all users.For more informatioon on the security content of this update see http://support.apple.com/kb/HT1222.
So I did.
Quite why my MacBook didn’t receive the security update automatically, I don’t know. Maybe I didn’t wait long enough. But with a security flaw as serious as this, which is reportedly being exploited, I would rather my laptop had been a little bit more in-my-face about the importance of me apply the patch rather than leaving the onus on me to go looking.